General
The customer must have a paid Company subscription.
SSO feature enabled by OpenBOM admin in the OpenBOM admin dashboard for company.
The SSO functionality applies only to the Web application, Workspace Manager, and SOLIDWORKS integrations. Other integrations and Drive applications are not supported yet.
User accounts must exist in BOTH OpenBOM Team account dashboard AND Azure Ad, or Okta (depends of SSO provider)
Questions or issues should be reported to OpenBOM support via the in-app Support button or sending email to support@openbom.com
Before starting the integration process, you should have an OpenBOM Company subscription, and you must have requested SSO function to be activated for your company.
You can use only one (single sign-on) SSO provider at a time.
Integrating with Microsoft Azure AD (Microsoft Entra ID)
Register OpenBOM application in Azure AD (Microsoft Entra ID)
Sign in to the Microsoft Azure portal. Click the menu icon at the top left corner to open the left side navigation pane.
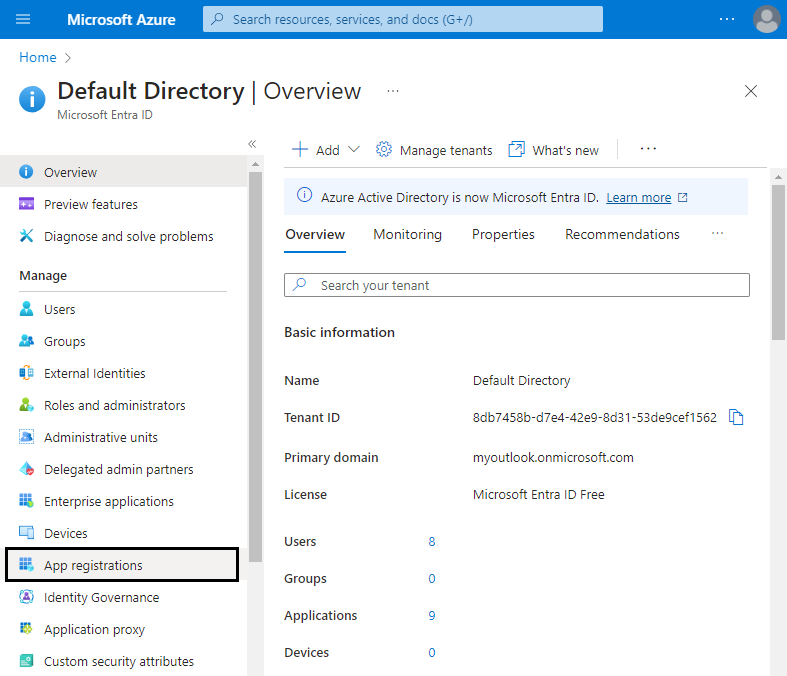
Select Microsoft Entra ID in the navigation pane.
Select App registrations in the new navigation pane that opens on the left.
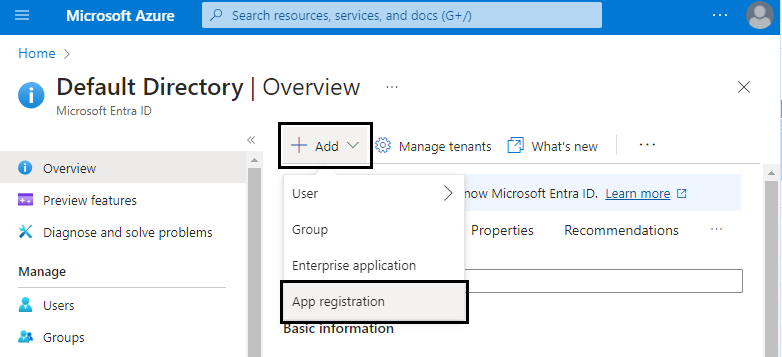
Add new registartion of application by clicking Add → App registration.
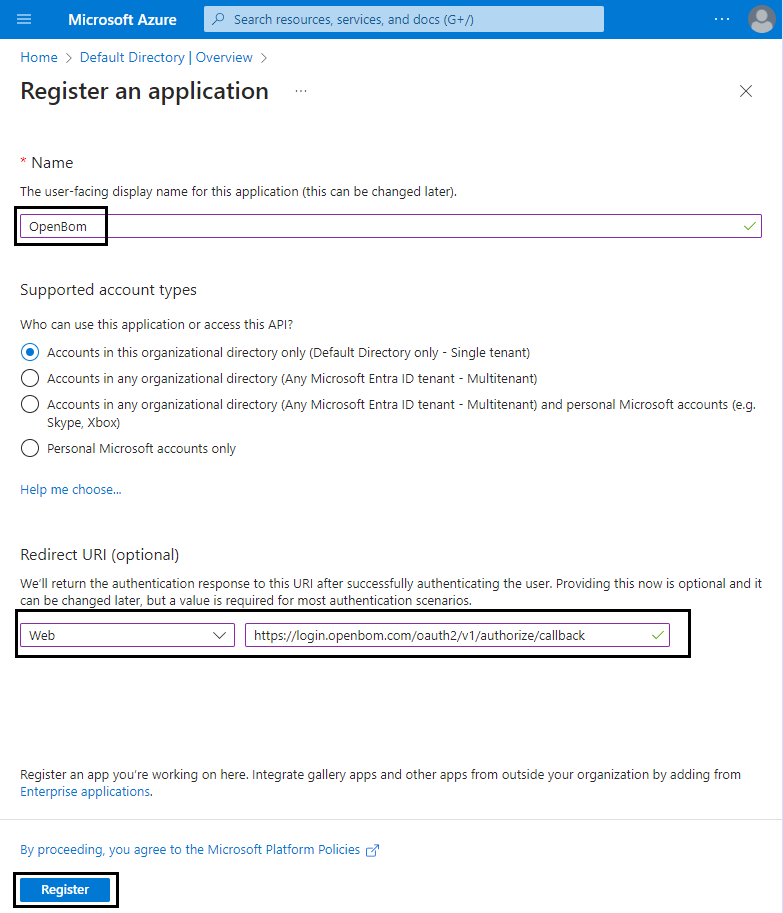
Register new application
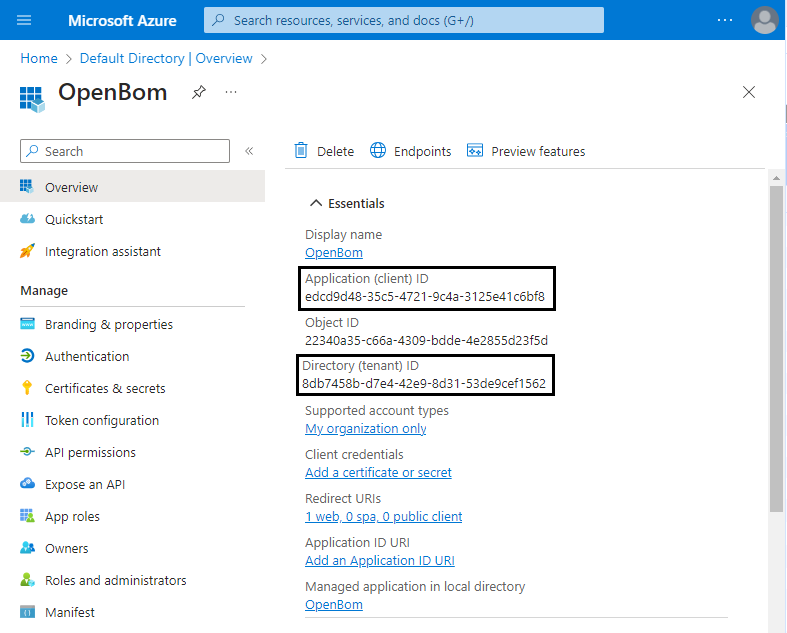
Set name to OpenBom, select Redirect URL to Web and set value to https://login.openbom.com/oauth2/v1/authorize/callback, and click Register.On the opened papge with registered application save values of Application (client) ID and Directory (tenant) ID.
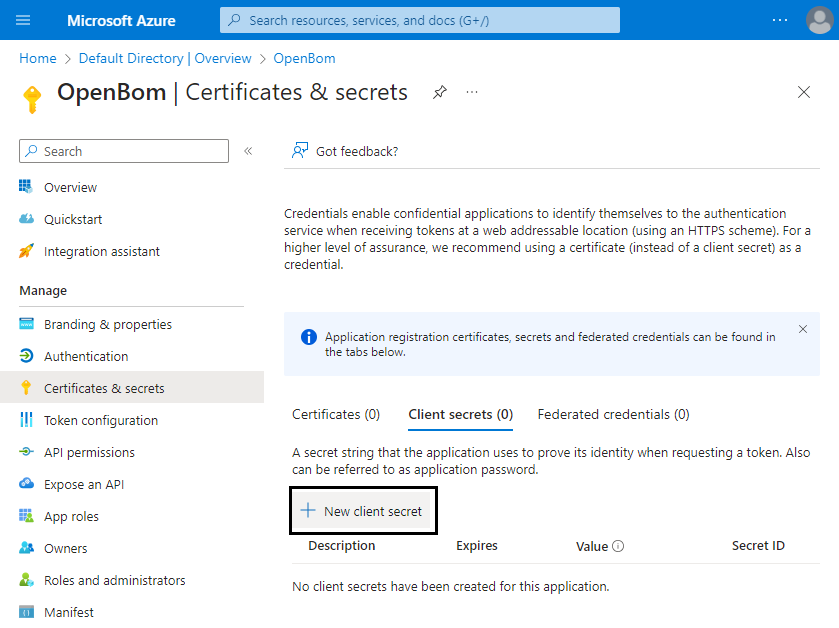
Select Certificates & secrets in the navigation pane to add Client Secret, and click New client secret.
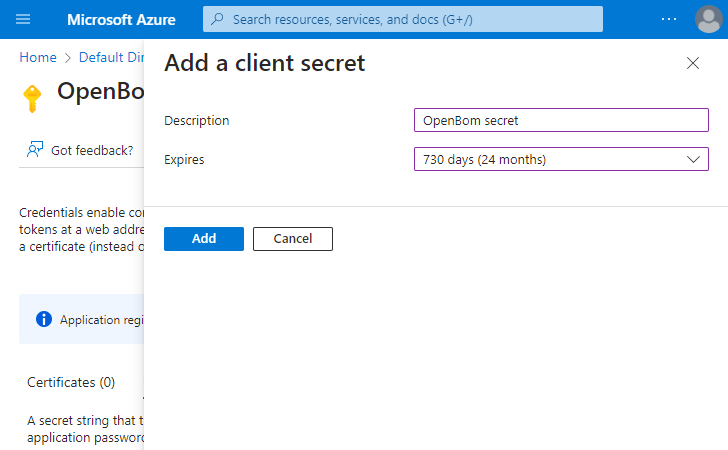
Add Client secret.
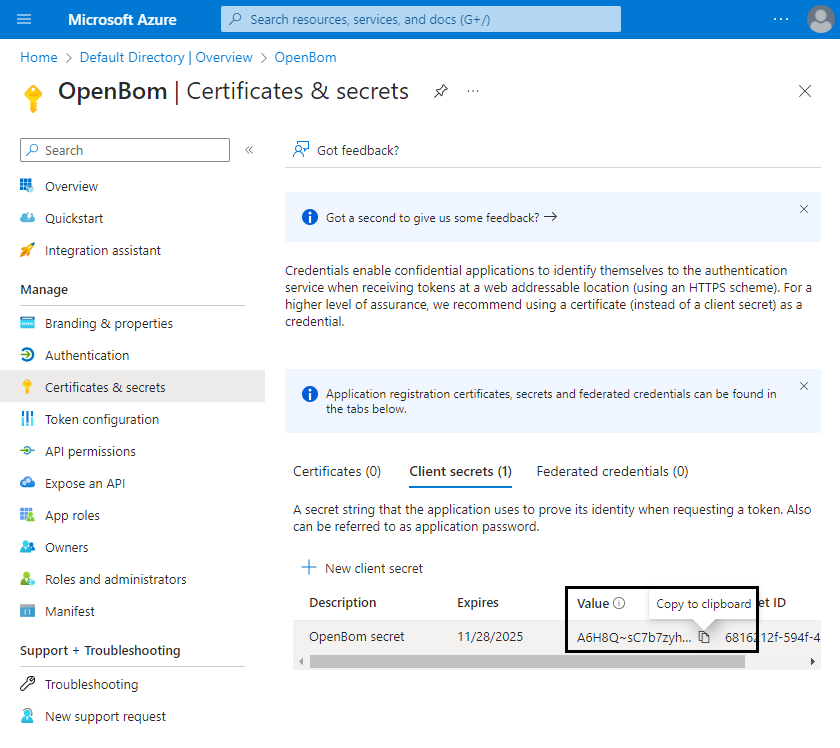
Save value of added Client Secret.
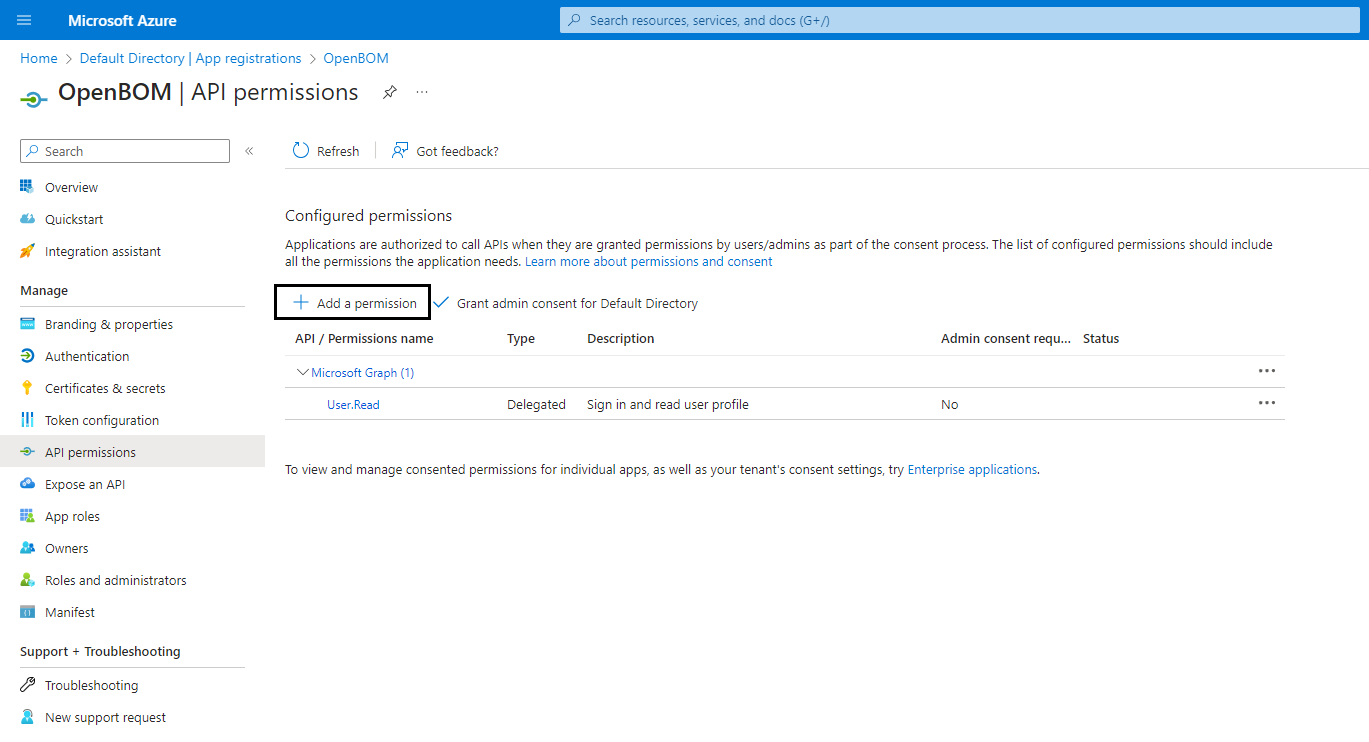
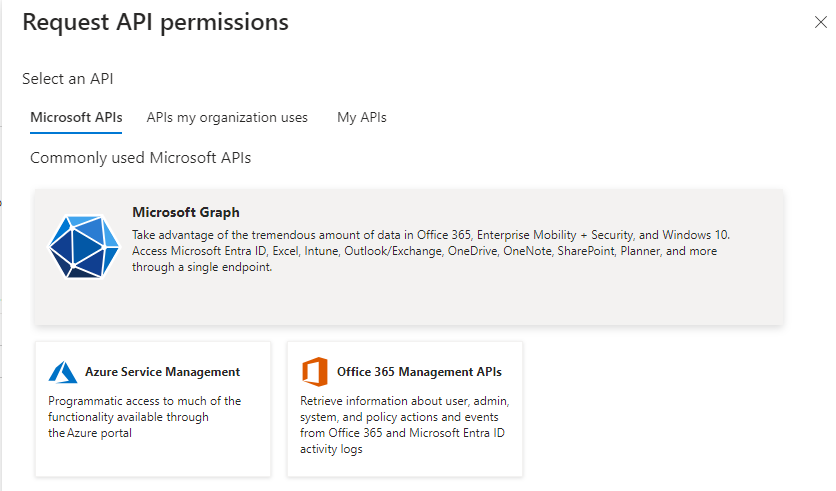
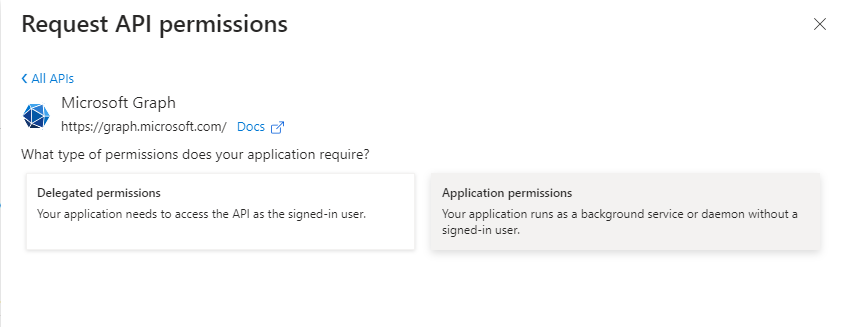
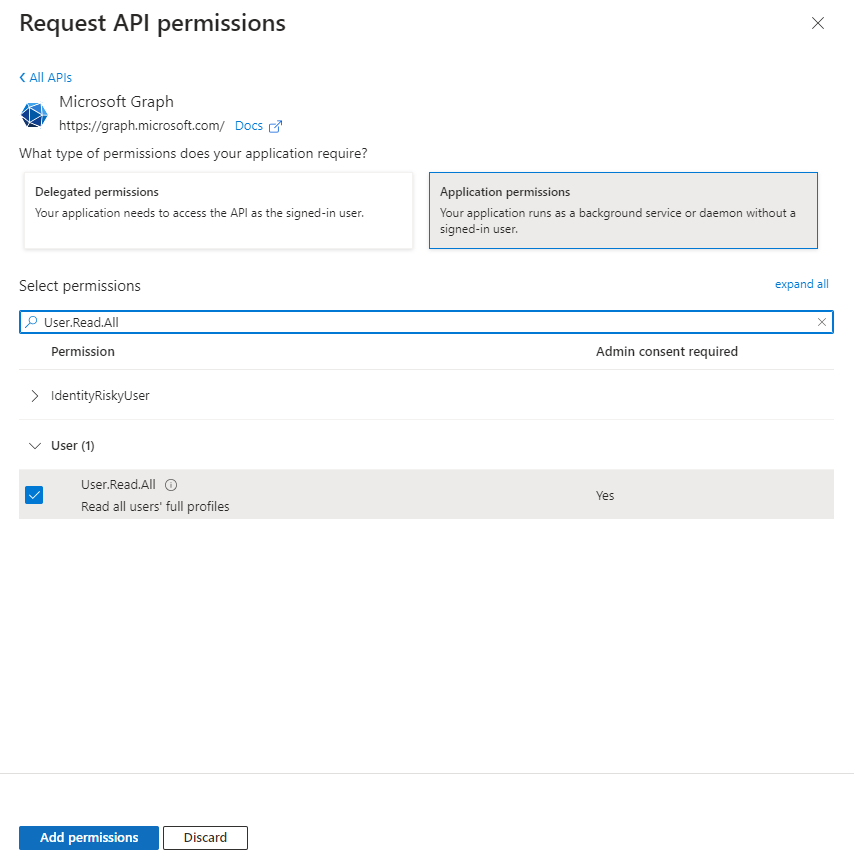
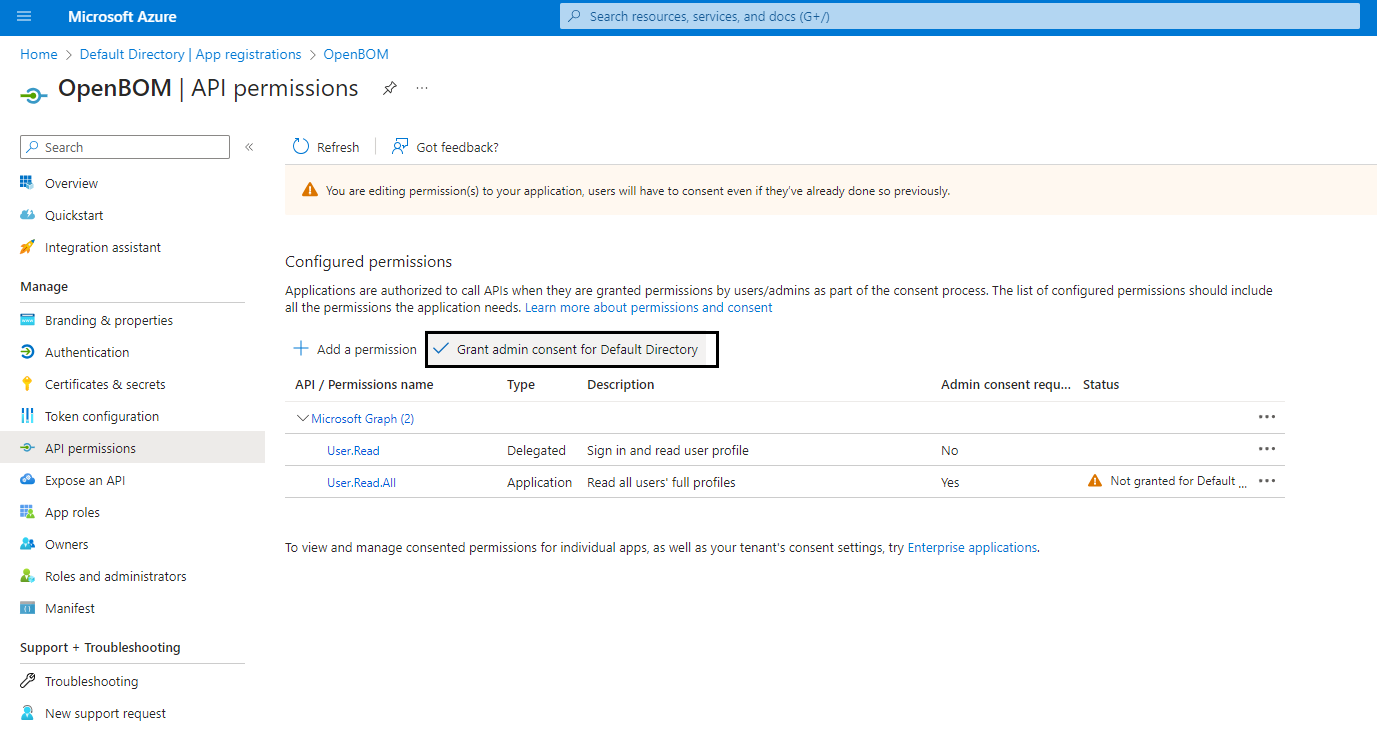
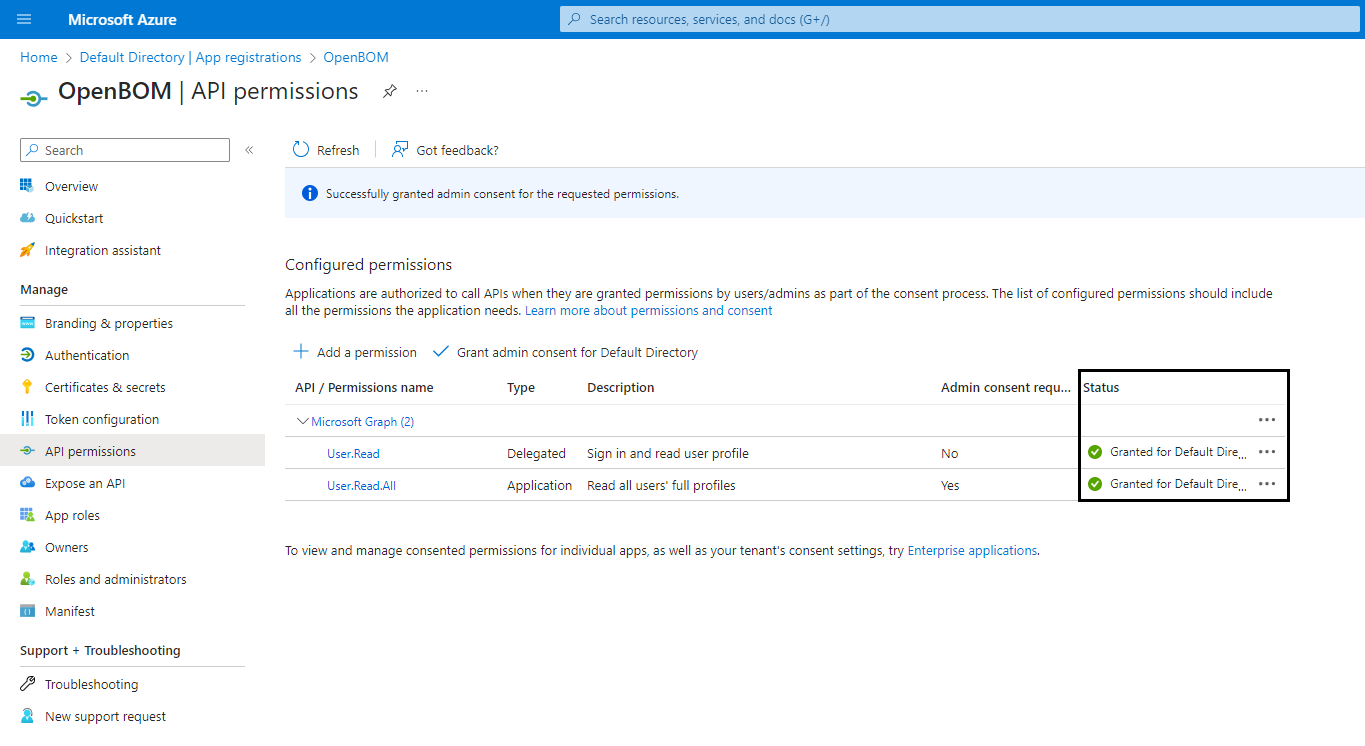
To allow users synchronization between Azure AD and OpenBOM, open API permissions in the navigation pane and add a pemission User.Read.All. OpenBom is uses only fields
mailandaccountEnabledfrom User profile in Azure AD.
Configuration in OpenBOM
Login as Company admin from your company to OpenBOM: https://bom.openbom.com/sign-in.
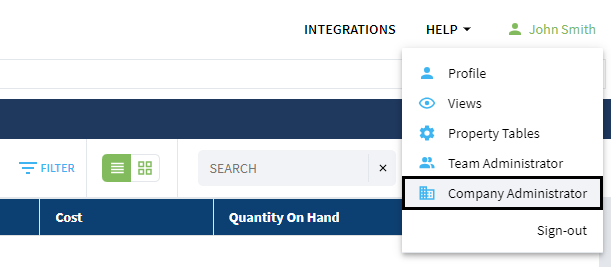
Open Company Administrator page.
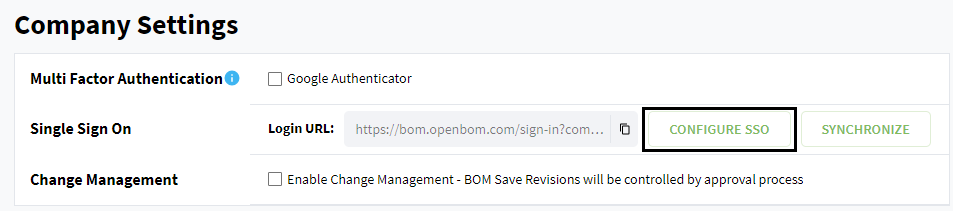
Company admin now has additional row Single Sign On. Click Configure SSO button.
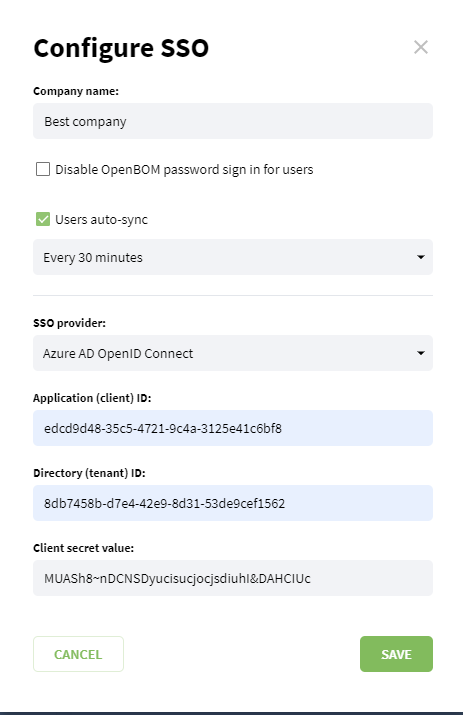
Enter values saved on the Step 6 and Step 9 of Azure configuration, and save configuration. Additionally put name of your company to Company name field.
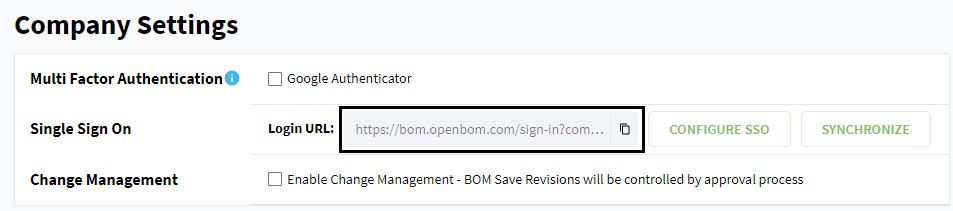
Copy Login URL for your company where you will have possibility to login with Single Sign On.
Logout from OpenBOM and open Login URL from previous step. Example of link:
https://bom.openbom.com/sign-in?company=946cef84-5e84-3bd3-6cef-120e843bd356Now you should see your company name and also Microsoft button to Single Sign On. Click on it to sign-in with Microsoft account from your Azure AD.
Integrating with Okta
Create OpenBOM application in Okta
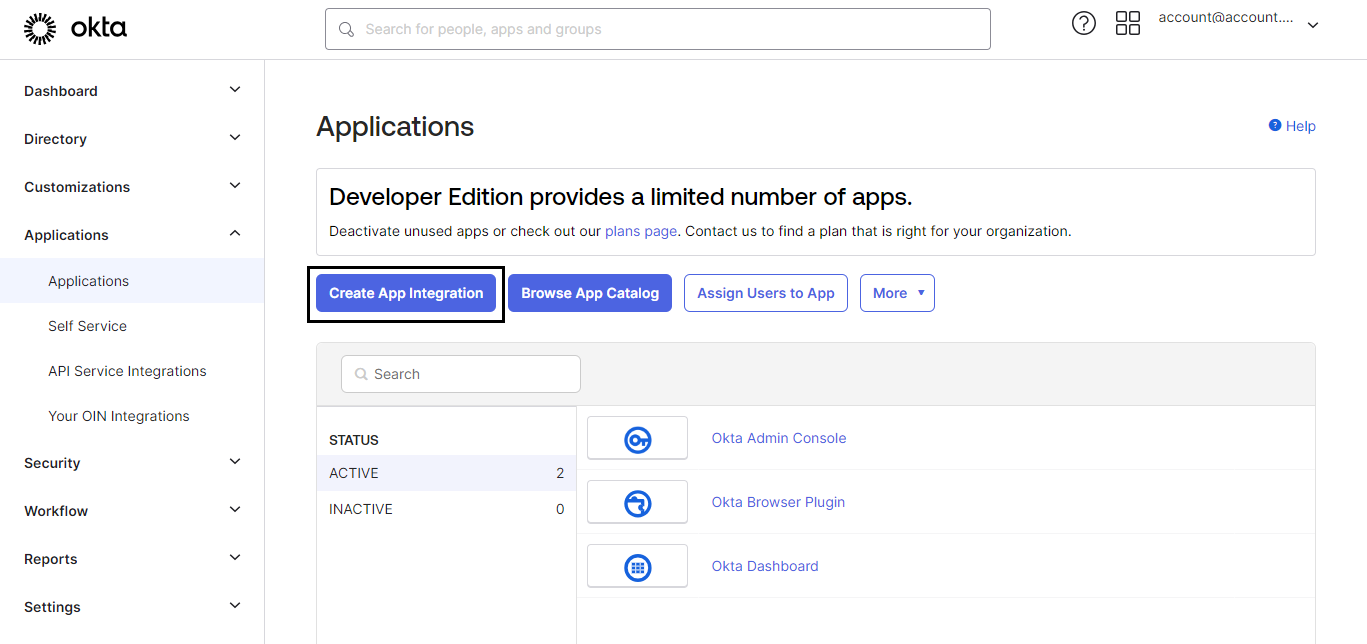
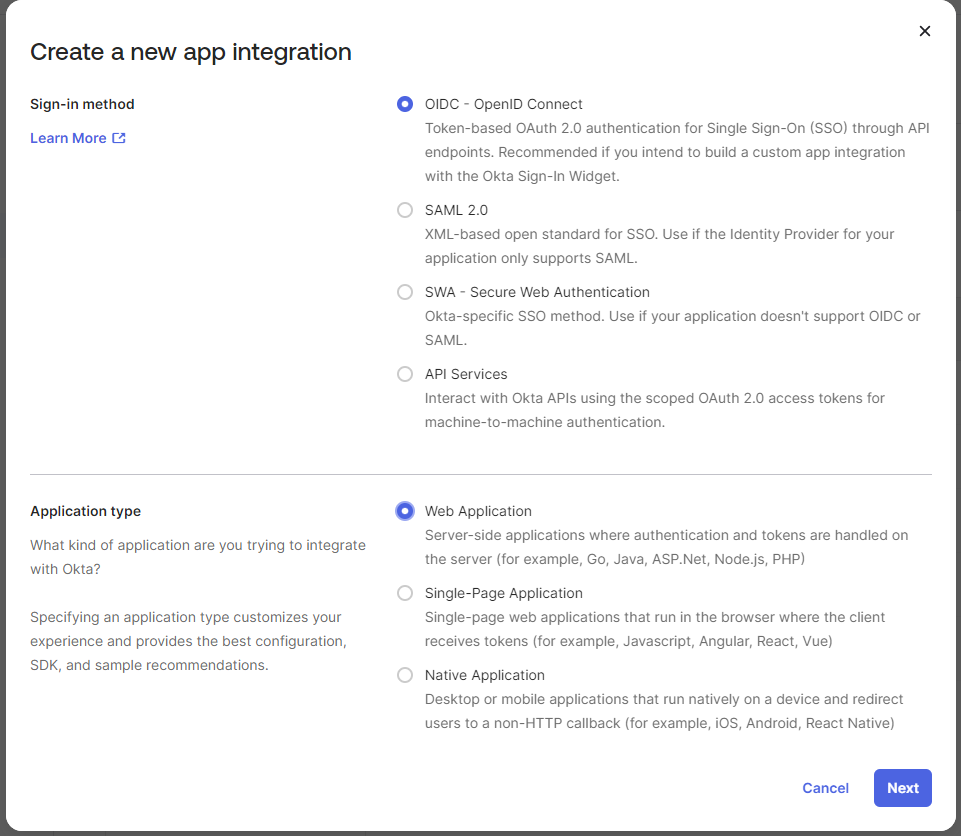
Sign in to your Okta dashboard. Go to Applications → Applications. Click Create App Integration
Select OIDC Sign-in method and Web application Application type
On the configuration page:
Put value https://login.openbom.com/oauth2/v1/authorize/callback to Sign-in redirect URIs.
Put value https://bom.openbom.com to Sign-out redirect URIs.
Additionally, select assignment mode for application.
Click Save.
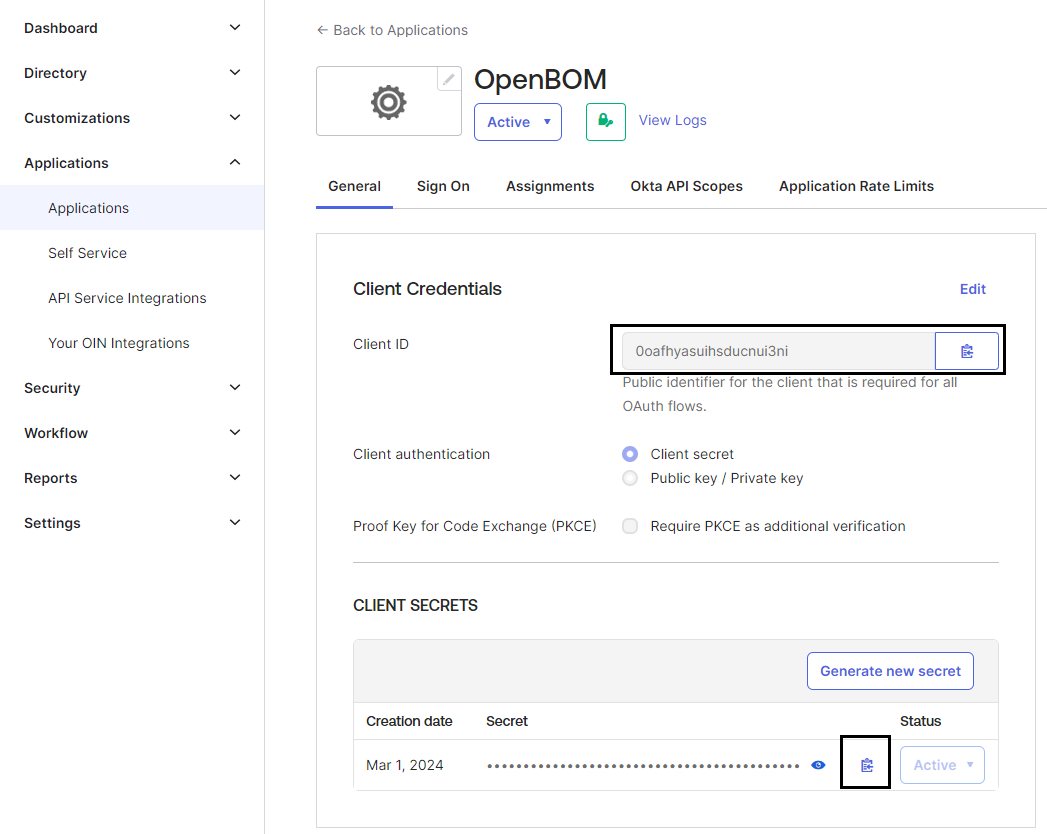
On the General tab of create application copy value of Client ID and Client Secret
Additionally get your Okta issuer URL like: http://dev-12345678.okta.com. It will be used in the configuration in OpenBOM.
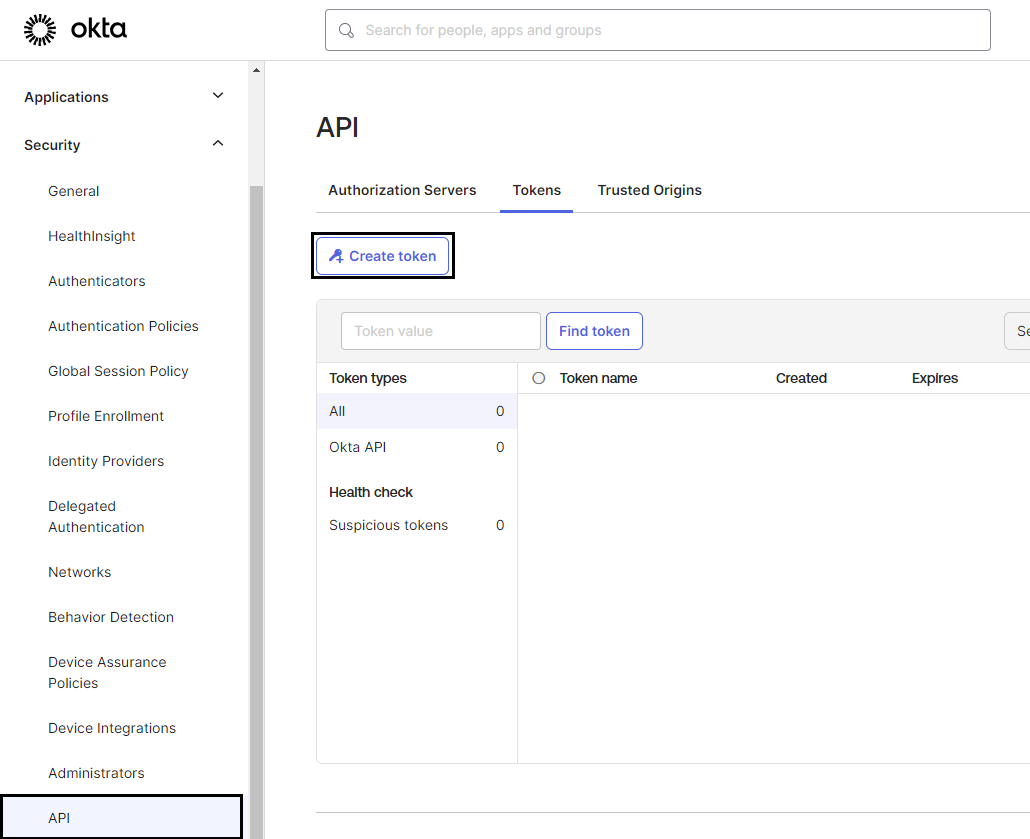
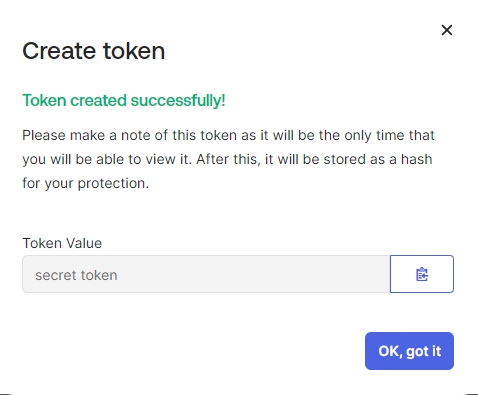
In case you need to synchronize users' status between your Okta and OpenBOM - additionally should be generated API key (this is optional). Go to Security → API page. Click Click Create token.
Token should be generated under user with required permissions to access users who will use OpenBOM. OpenBOM is taking only users emails and users' status from customer Okta, no other information is taken.
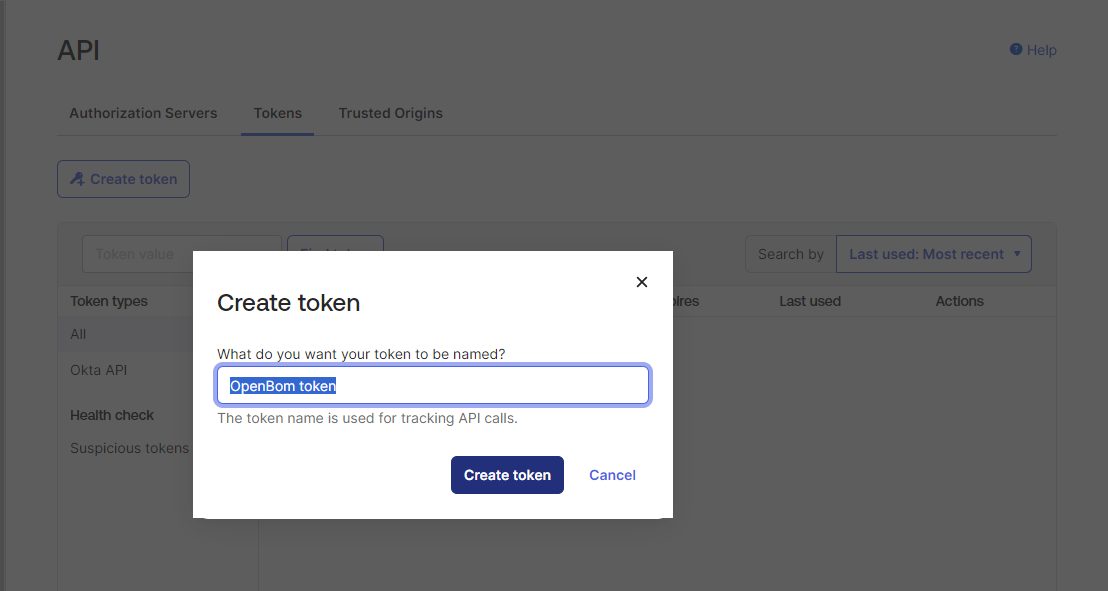
Enter name for token and click Create token
Save the value of the token, it will be used for the configuration of SSO in OpenBOM.
Configuration in OpenBOM
Login as Company admin from your company to OpenBOM: https://bom.openbom.com/sign-in.
Open Company Administrator page.
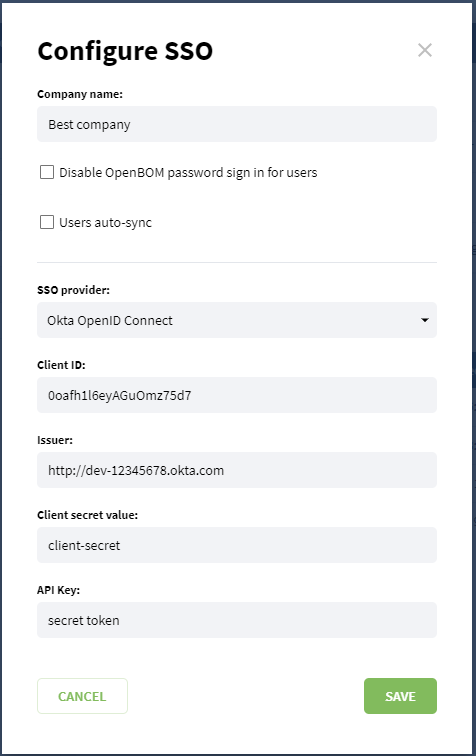
Company admin now has additional row Single Sign On. Click Configure SSO button.
Enter values saved on the Step 4 and Step 8 of Okta configuration, and save configuration. Additionally put name of your company to Company name field.
Copy Login URL for your company where you will have the possibility to login with Single Sign On.
Logout from OpenBOM and open Login URL from the previous step. Example of link:
https://bom.openbom.com/sign-in?company=946cef84-5e84-3bd3-6cef-120e843bd356Now you should see your company name and also Okta button to Single Sign On. Click on it to sign-in with your Okta account.
Additional features available in SSO configuration
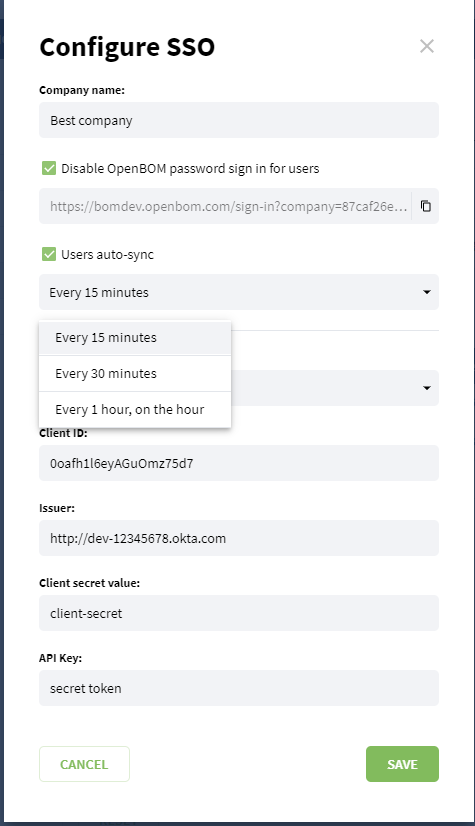
In Configure SSO page it can be found additional options for SSO configuration: disable password for users, and configure auto-sync for users status..
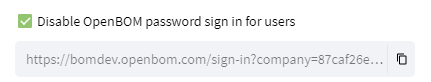
Disable OpenBOM password sign in for users
In case this flag is selected and the configuration saved - we disable users in the company login with their passwords created in OpenBOM (except OpenBOM company administrator). We delete passwords for users in the company, and users will able login to OpenBOM only using company SSO provider (Azure AD or Okta). Company admin still will be able to log i from the URL for admins, URL for admin will be provided in configuration once the flag is enabled. Users will not be able to reset their password if the password is disabled. Once this flag is checked out and the configuration saved - users will be able to reset their password and login to OpenBOM using a newly created password by them.
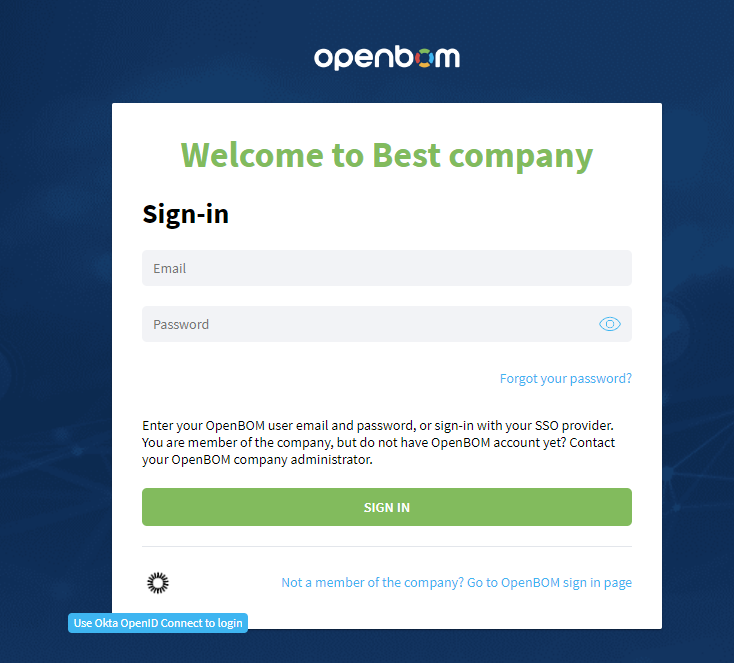
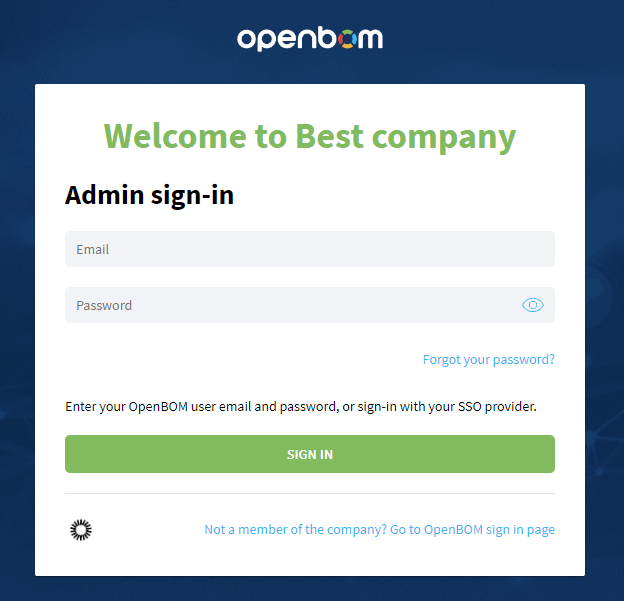
In case password is disabled for the company, users will see next sign-in company page:
Company admin will still be able to login with password using page for admin sign-in:
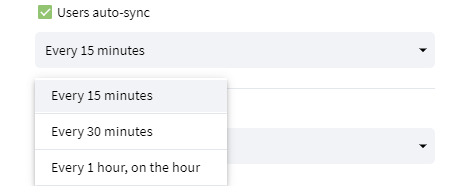
Users auto-sync
In case Users auto-sync flag is enabled, the company admin can select how often synchronization will be done. We have 3 options:
every 15 minutes (at 0, 15, 30, and 45 minutes every hour);
every 30 minutes (at 0, and 30 minutes every hour);
every 1 hour (at 0 minutes every hour).
Company admin can do this operation manually in Company dashboard in OpenBOM.
During synchronization users not present or disabled in Azure AD or Okta will be disabled in OpenBOM. Users that were present in OpenBOM and were added to Azure AD or Okta after that, will be enabled in OpenBOM.
For new accounts in OpenBOM - company admin for now should create an account in OpenBOM manually within this release of SSO. This means that if an administrator adds a user to Azure AD or Okta, he must also add the user to the OpenBOM team.